select the best answer. which of the following are breach prevention best practices
Confidentiality integrity and availability are the fundamental objectives of health information. All of the above Which of the following are breach prevention best practices.

30 Best Practices For Preventing A Data Breach Securityscorecard
Established a national set of standards for the protection of PHI that is created received maintained or transmitted in electronic media by a HIPAA covered entity CE or business.

. A single technology cannot provide complete. Access only the minimum amount of PHIpersonally identifiable information PII necessary. Promptly retrieve documents containing PHIPHI.
A breach as defined by the DoD is broader than. The following best practices may help. Which are breach prevention best practices.
Best practices for breach prevent are. Logoff or lock your workstation when it is unattended. Select the best answer.
Remediation Accessed N PHI transmitted orally PHI on paper PHI transmitted electronically correct All of the above-----11 Which of the following are breach prevention best. Which of the following are breach prevention best practices Saturday June 11 2022 Edit. Administrative safeguards are administrative actions and policies and procedures that are used to manage the selection development implementation and.
The following are high-level best practices for preventing breaches. Train Employees on Security Awareness. Access only the minimum amount of.
Developing the IRP will help the IT staff of the company to control the data breach incidents. Best practices for breach prevent are. In which of the following circumstances must an individual be given the opportunity to agree or object to the use and disclosure of their PHI.
Focusing on the security measures of your company is very important. Access only the minimum amount of PHIpersonally. Which of the following are breach.
Top 4 Human Errors In Cyber Security How To Prevent. Which of the following are breach prevention best practices. Access only the minimum amount of PHIpersonally identifiable information PII necessary.
Terms in this set 20 Under HIPAA a covered entity CE is defined as. Identify areas that store transmit collect or process. Select the best answer.
Invest in security automation. In the age of digital data keeping information safe is more important than ever. See answer 1 Best Answer.
Promptly retrieve documents containing PHIPHI from the printer. All of this above. The employees play an essential responsibility in keeping their.
30 Best Practices for Preventing a Data Breach Identity sensitive data collected stored transmitted or processes. Logoff or lock your workstation when it is unattended. Which of the following are breach prevention best practices.
The correct answer is A. See answer 1 Best Answer. The following are breach prevention best practices.
Logoff or lock your workstation when it is unattended. Properly configure the cloud. 1 who has lead responsibility.
All of this above True or False. What are breach prevention best practices. A breach as defined by the DoD is broader than a HIPAA breach.
Which of the following are breach prevention best practices.
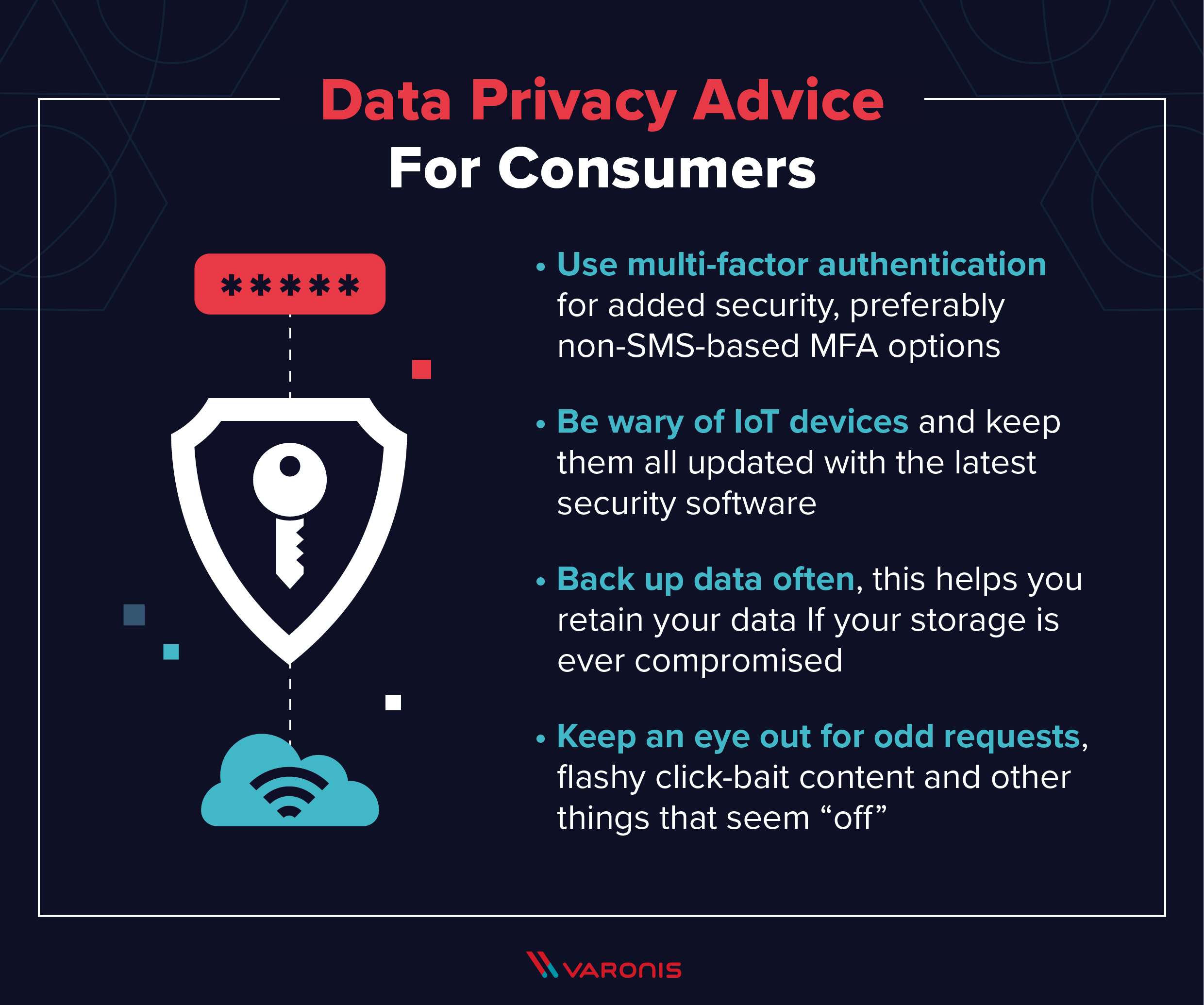
Data Privacy Guide Definitions Explanations And Legislation
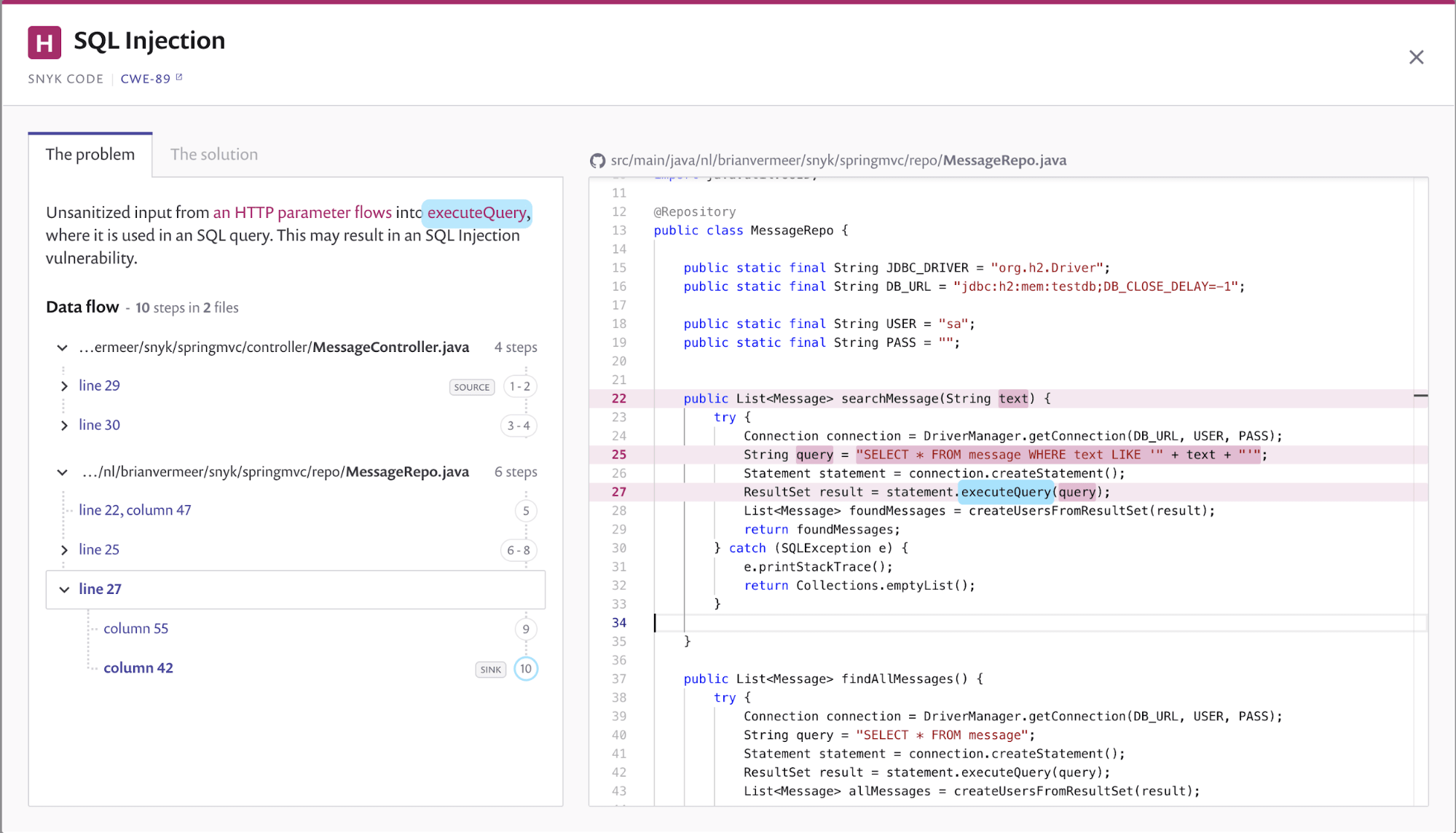
8 Best Practices To Prevent Sql Injection Attacks Globaldots
Cybersecurity Risk Management Frameworks Analysis Assessment Imperva

Data Loss Prevention Best Practices Endpoint Protector

5 Ways Big Companies Protect Their Data Endpoint Protector

What Is Data Security Definition Planning Policy And Best Practices Spiceworks 1

13 Ways To Prevent Data Breaches In Healthcare

Which Of The Following Are Breach Prevention Best Practices Public Health

Data Masking Techniques And Best Practices For Data Security Nightfall Ai

How To Choose The Best Password Manager Avast

Data Loss Prevention What Is Dlp How Does It Work

What Is A Data Breach How To Prevent One

Securitymetrics Guide To Hipaa Compliance

Data Loss Prevention Next Steps

Top 10 Ecommerce Fraud Detection And Prevention Best Practices For 2021 Spiceworks 1

Top 5 Internal Data Security Threats And How To Deal With Them Endpoint Protector

Securitymetrics Guide To Hipaa Compliance

What Is Fraud Detection Definition Types Applications And Best Practices Spiceworks 1

13 Best Siem Tools In 2022 Vendors Solutions Ranked Paid Free